SANS Institute, EMEA on X: "#CloudSecurity Poster: Cloud Security and DevSecOps Best Practices This poster describes top cloud security and Kubernetes issues along with free, open source tools that can be used
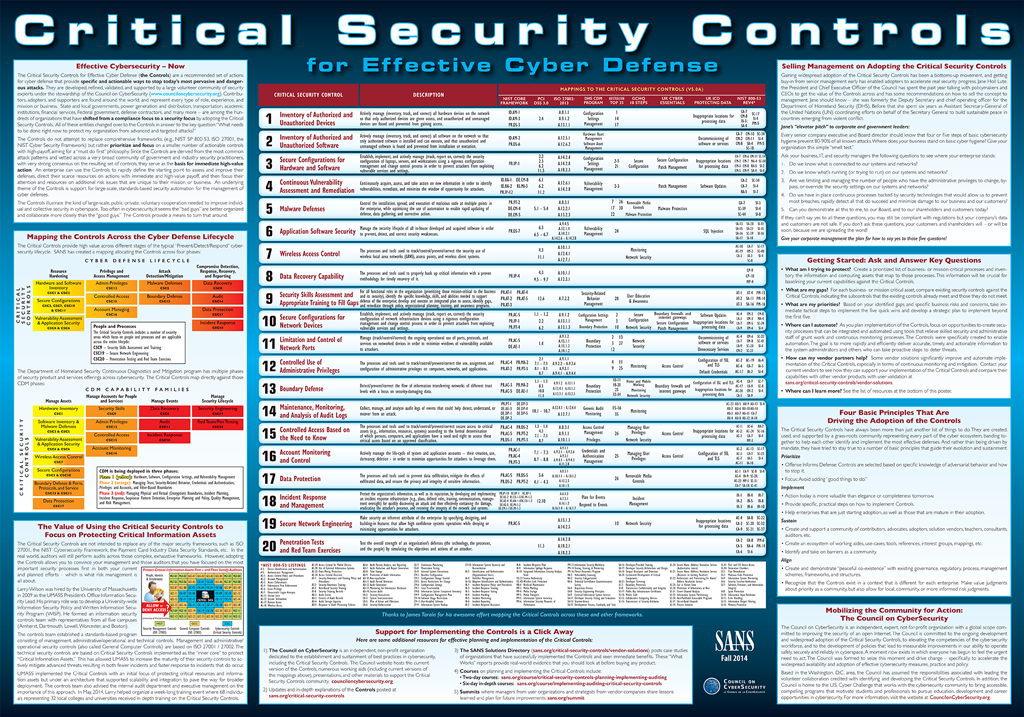
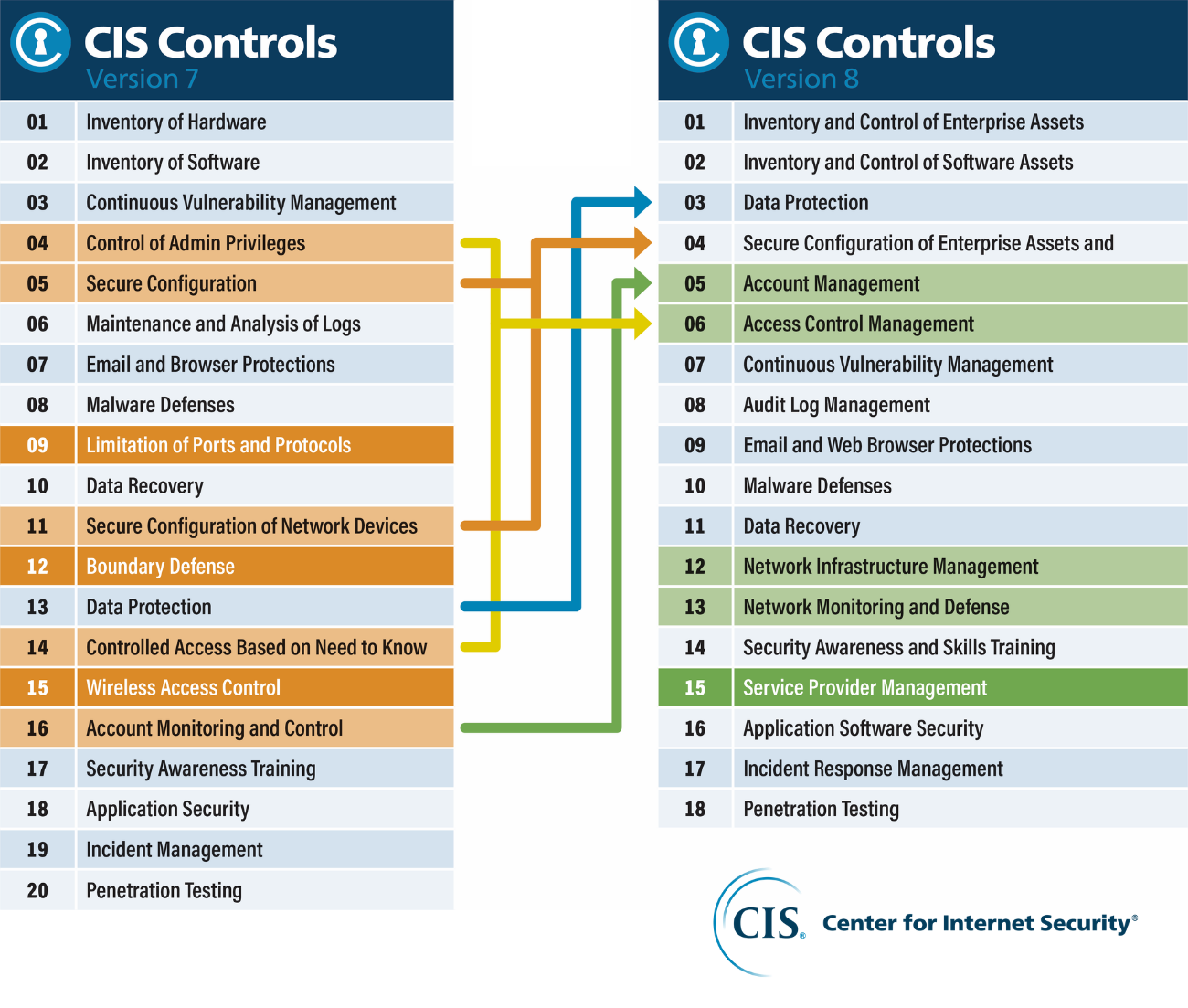
SANS Institute on X: "20 CRITICAL SECURITY CONTROLS | POSTER: Set of actions for cyber defense. DL > PDF (2pgs) - http://t.co/YZGlCbuXmd http://t.co/moeIozrqu0" / X

SANS Institute on Twitter: "We're counting down the #20CoolestCareers in #Cybersecurity #SSA #15 -#SecurityAwareness Officer (retweet if this is your job role) Want to identify top human risks and the behaviors in

Undertale SANS Institute CWE/SANS TOP 25 Most Dangerous Programming Errors Art Keyword Tool, PNG, 730x1095px,

Lesson 9 Common Windows Exploits. UTSA IS 3523 ID and Incident Response Overview Top 20 Exploits Common Vulnerable Ports Detecting Events. - ppt download

System Defense Defending Home Networks. Introduction Computer Security What it's not Person, Place or Thing What it is Independent –Of Network OS –Of. - ppt download